Hack the Box - Da Vinci
Created by nickvourd
Background information
Da Vinci is a challenge hosted on Hack the Box. I downloaded the DaVinci.zip and extracted it using the password provided (hackthebox) which left 3 files; monalisa.jpg, Plans.jpg and Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg.
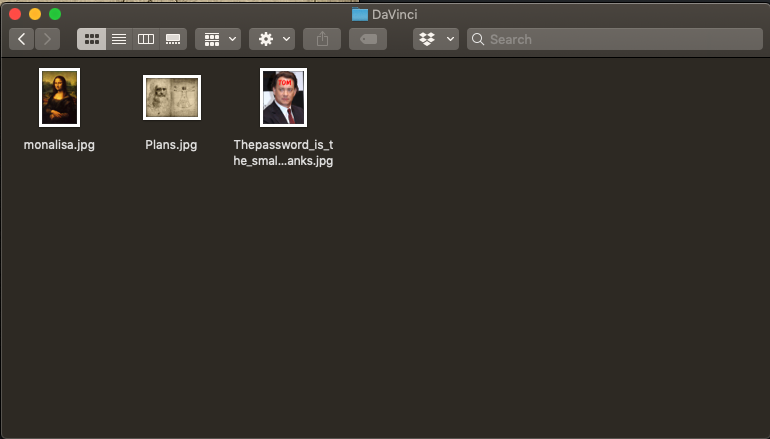
Decompressed DaVinci.zip
Challenge Description
Try to find out the secret which is hiding inside of these pictures and learn the truth about Mona Lisa!
Method
Step 1. Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg
I decided to tackle each image individually and first began with the file Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg as there was a obvious clue of "The password is the small name of the actor named Hanks" and the image had "TOM" written on Tom Hanks’ head.

Thepassword_is_the_small_name_of_the_actor_named_Hanks.zip
I decided to use a tool called steghide which would allow me to see if there was any files embedded into the image. steghide required a password, so I tried different variations of "tom" and eventually extracted a file called [email protected] using the password "TOM"
steghide Command
steghide extract -sf Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg
Enter passphrase: TOM
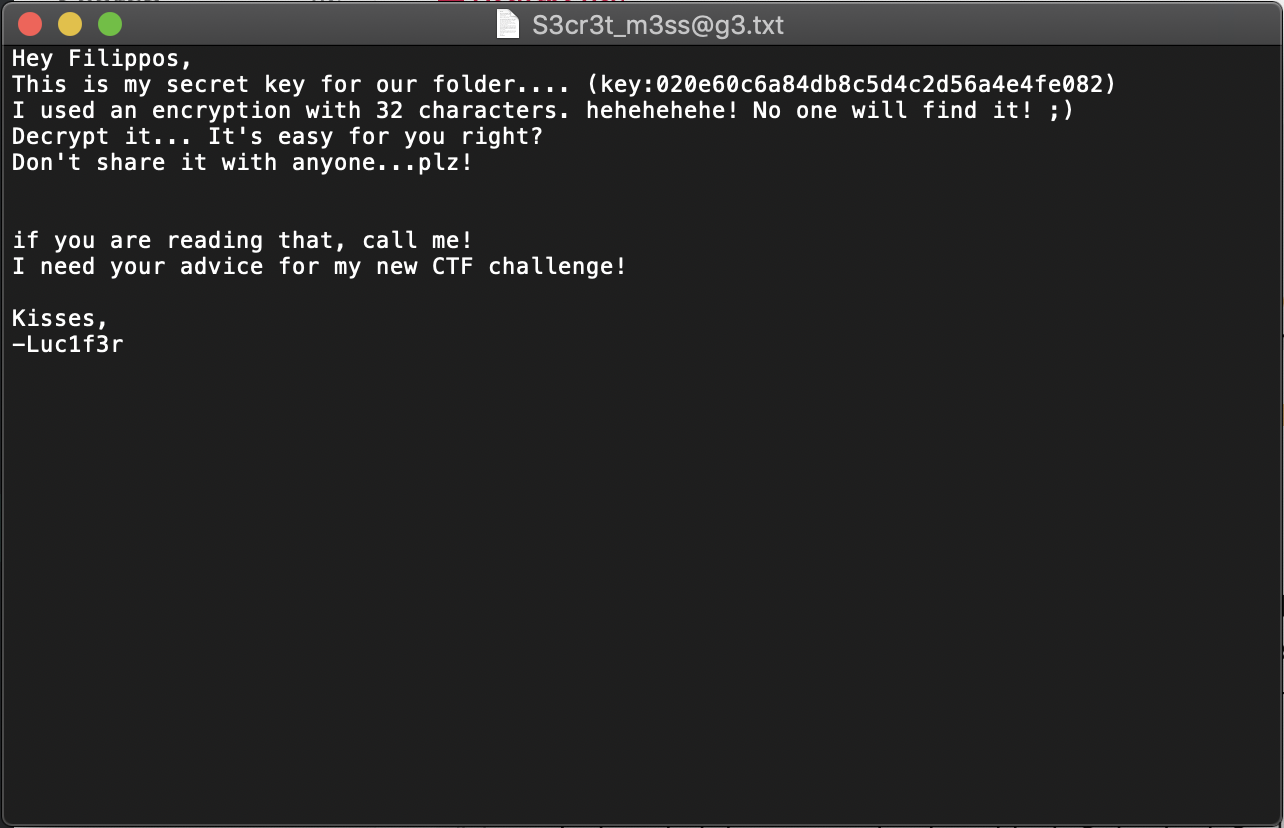
wrote extracted data to "[email protected]".Inside this file was an md5 hash (020e60c6a84db8c5d4c2d56a4e4fe082) which decrypted to leonardo.
Step 2. Plans.jpg
After obtaining another password (leonardo) I attempted to run steghide on all of the images using this password however no other files could be extracted. I opened the Plans.jpg to see if there was any interesting information photoshopped into it, however it appeared to be a copy of a page from a book.
Plans.txt
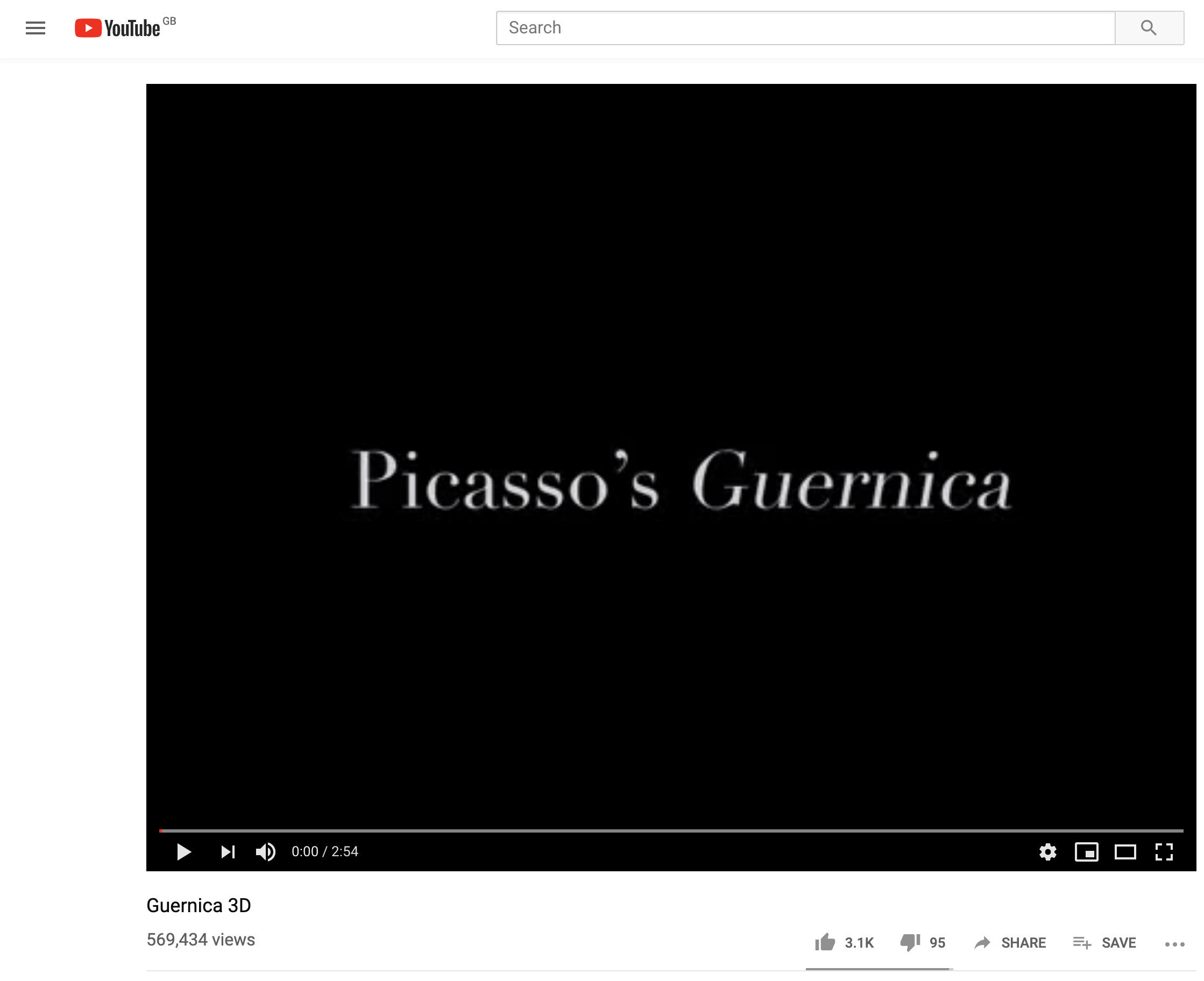
I decided to see if any information was hidden in the metadata image, so I ran the exiftool on Plans.jpg which returned no interesting information. I decided to use the cat command and found a link to a YouTube video with the title of "Guernica 3D", watching the video did not provide me with any hints so I decided to move onto another image.
Step 3. monalisa.jpg
There was one file I had not yet investigated which was a picture of Mona Lisa.

monalisa.jpg
I ran a few commands on the file to see if I could extract anymore information or files which could help with this challenge. The steghide command did not let me extract any files and the exiftool did not produce any interesting information so I decided to try and unzip the file using the md5 encrypted word "leonardo" which extracted a file called "famous.zip".
unzip Command
unzip -P leonardo monalisa.jpg
Archive: monalisa.jpg
warning [monalisa.jpg]: 450363 extra bytes at beginning or within zipfile
(attempting to process anyway)
inflating: famous.zipStep 4. Finding the Flag
I attempted to unzip the "famous.zip" file using "leonardo" as the password and I managed to extract another file called Mona.jpg.

Mona.jpg
I then used the steghide command again on Mona.jpg trying known passwords however did not manage to extract any files. I decided to go back to watch the YouTube video which kept talking about the painting called "Guernica". I then attempted to extract the files again using steghide with the password Guernica 3D (title of the video), however I still got errors. I then used "Guernica" which extracted a file called "key"
steghide Command
steghide extract -sf Mona.jpg
Enter passphrase: Guernica
wrote extracted data to "key".Step 5. Decrypting the Flag
The key file contained the following:
VTBaU1EyVXdNSGRpYTBKbVZFUkdObEZHT0doak1UbEZUVEJDUldaUlBUMD0=I pasted this into CyberChef and used the "magic" function which decrypted the code to present me with "HTB{M0n@L1z@!s_D3@D}" which I submitted as the flag.
Passwords
| File | Password |
|---|---|
| Thepassword_is_the_small_name_of_the_actor_named_Hanks.jpg | TOM |
| monalisa.jpg | leonardo |
| famous.zip | leonardo |
| Mona.jpg | Guernica |
| HTB Flag | HTB{M0n@L1z@!s_D3@D} |