Hack the Box - Find The Easy Pass
Created by Thiseas
Description
Find The Easy Pass is a reverse engineering challenge hosted on Hack The Box.
Challenge Description
Find the password (say PASS) and enter the flag in the form HTB{PASS}
Downloading and decompressing the zip presents an executable. Running the program provides a form asking for a password to be entered, if the password is wrong a popup appears saying "Wrong Password!".
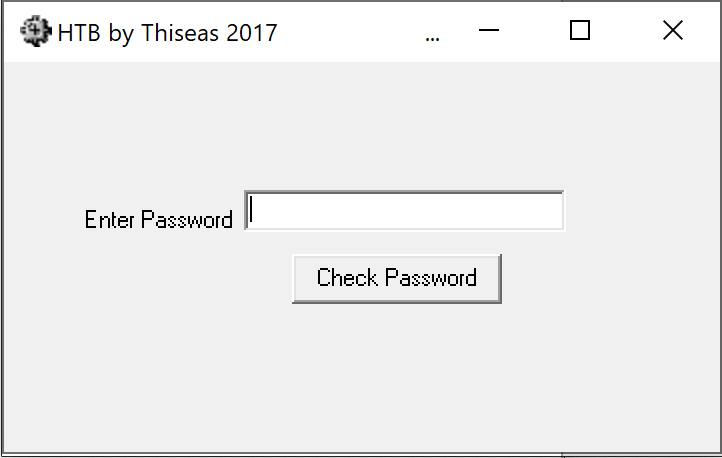
Running the Executable

Results from entering a random input
Method
Step 1. PEiD
My first step was to use a tool called PEiD to see how the program was being compiled.
PEiD Results
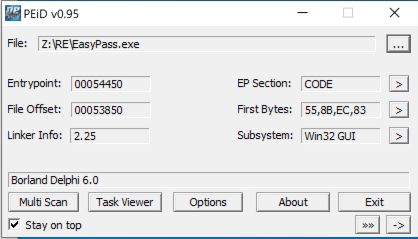
PEiD output
PEiD stated that the executable was compiled by using Borland Delphi 6.0. This is an event driven programming language which provides compilers to generate native code for Microsoft Windows, macOS, iOS, Android and Linux.
Step 2. OllyDBG
My next step was to load the executable into a program called OllyDBG. This is a 32-bit assembler level analysing debugger for Microsoft Windows.
Analysis
When first investigating the disassembled code, I noticed that the entry point to the executable would perform some basic setup steps then call an "EasyPass" function.
Following the function, it appeared to be loading and generating the Windows form of the application.
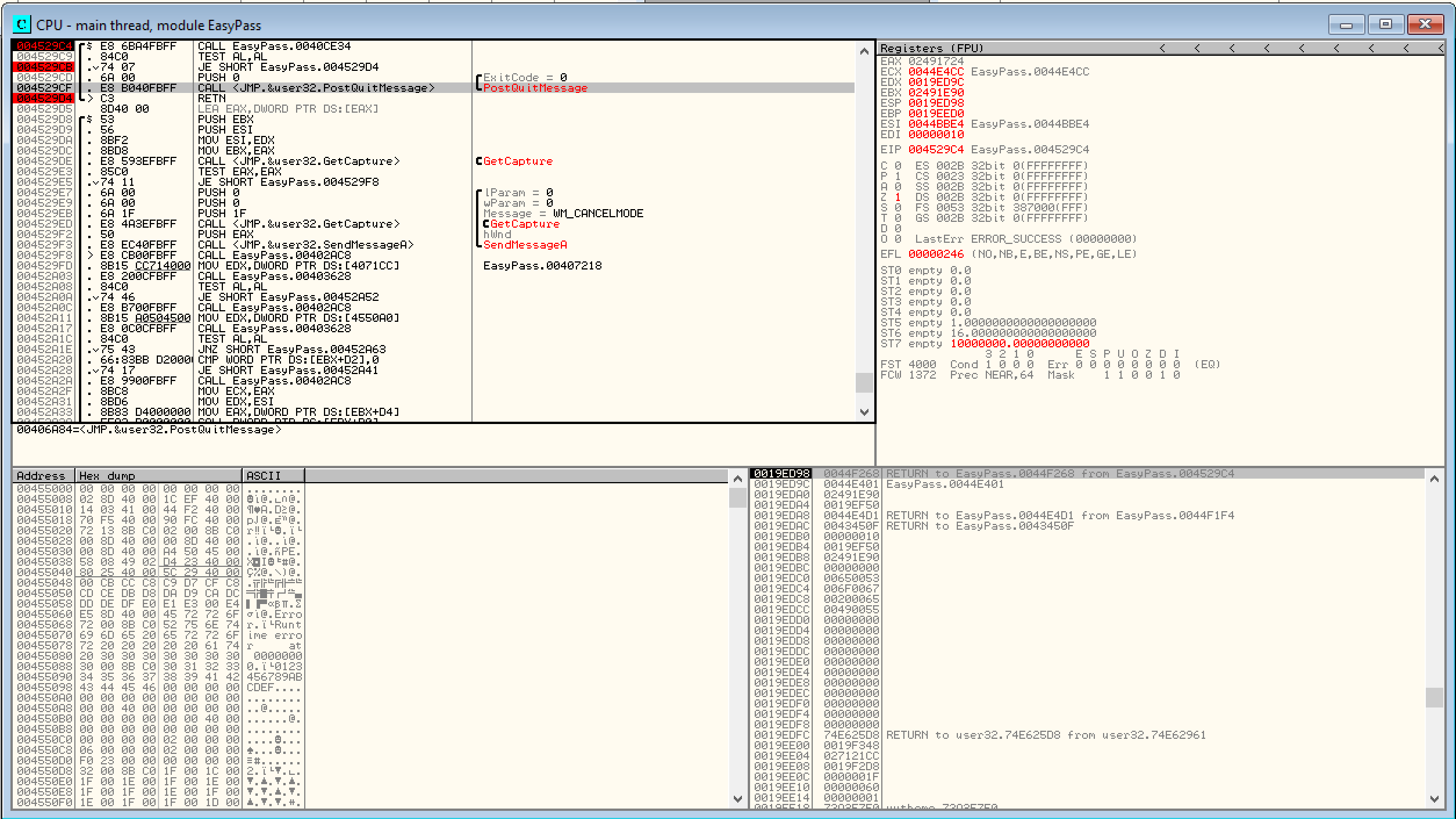
OllyDBG output
Generate Strings
I was unable to spot any indication of the password check so decided to generate all the strings to see the position of the "Wrong Password!" string. After running "All Referenced Strings" on the main "EasyPass" function, I found the "wrong password!" string located at position 00454144, I also found a "Congratulations" string located at position 00454138. I added breakpoints to both of these positions.
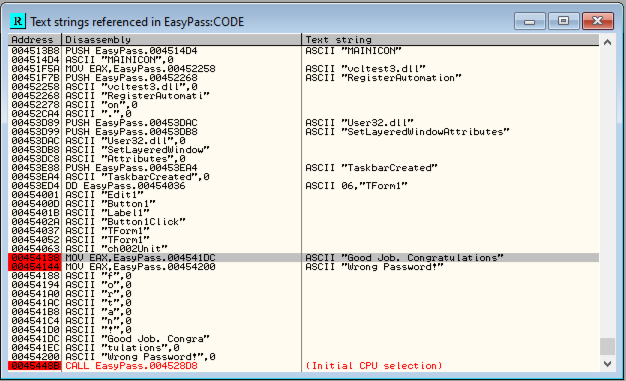
OllyDBG strings output
Step Through
I re-ran the program which stopped at the breakpoint 00454144. I found the function which checked the passwords matched and decided to investigate the function and added a breakpoint to the script. I re-ran the program and used the step-through function to view what was happening. I found a string called "fortran!" which was being compared to the string "test" (my program input).
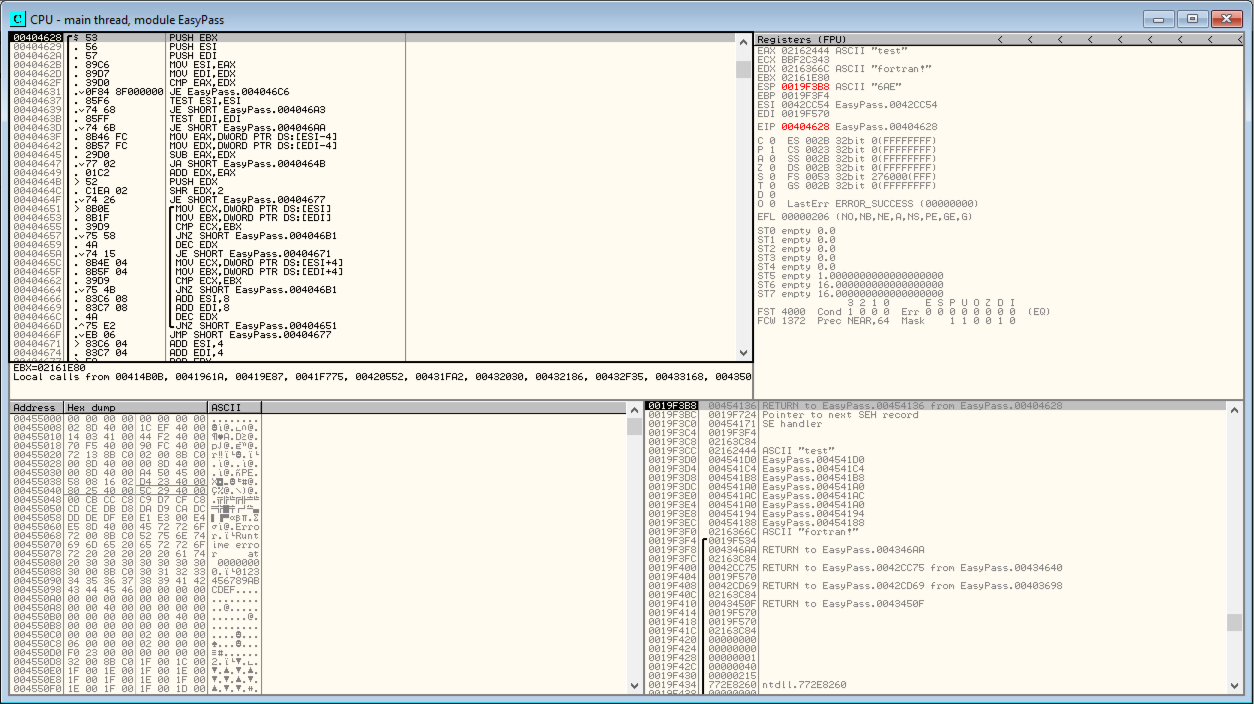
OllyDBG password match
Checking the password
I then ran the program and entered "fortran!" as the password which gave me the "Congratulations!" popup. As the challenge description said that the password would be the Hack the Box flag, I entered "HTB{fortran!}"" into the Hack the Box flag input which allowed me to complete the challenge.
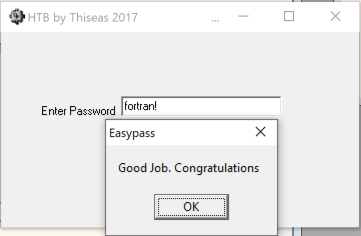
Successful password
| HTB Flag |
|---|
| HTB{fortran!} |